Active Directory Password Reset Security
Creating and distributing passwords through automation to outside networks requires the highest attention to and emphasis on security. Bright Pattern has addressed these concerns at each point of the process to ensure the protection of customer data and resources.
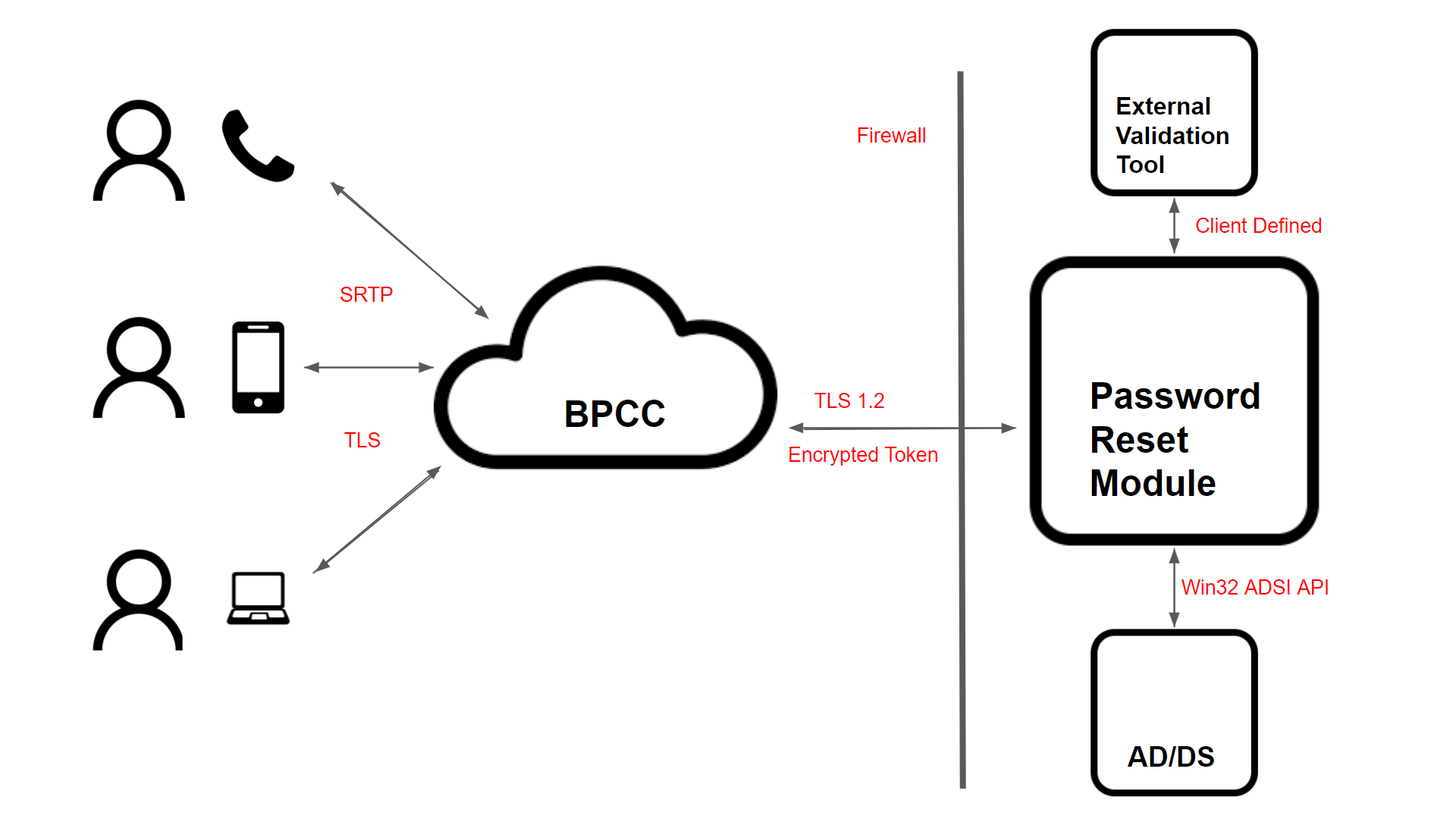
User Devices Connecting to BPCC
Users resetting their passwords can do so over voice from their phones, SMS from their mobile devices, or using webchat from their browsers. Each of these methods has been secured and adheres to the protocols governing their usage. For webchat and SMS, TLS 1.2 (or higher when available) encryption is used. Mobile connections support encryption specified by the carrier and web-based calls are protected by SRTP.
User Authentication to BPCC
Bright Pattern supports multiple methods for users to authenticate prior to generating a password request. Depending on the requirements and design of the client, BPCC can verify if a user is calling or messaging from a known device. BPCC can also utilize information from the ITSM database and compare it with user responses to ID numbers or PINs. For authentication on multiple devices, BPCC can generate a secret key and send it to a user on a different device. Also, BPCC integrates with biometric authentication services from Microsoft Azure. This set of verification tools can be used to ensure that the user requesting the password is properly authenticated.
BPCC Connecting to Client Password Reset Module
The Password Reset Module (PRM) runs behind the network firewall of the client environment and listens for requests on a specified port (i.e., 8080 by default). An exception specific to this application and port is necessary to allow communication between BPCC and the PRM, while the firewall remains active protecting all other traffic.
In order for a connection to be established with the PRM, a token must be provided to verify the requester is a known and trusted service. This token can be of any length within a 128-character limit and can be encrypted using a time-based hash for additional security. The data sent between the PRM and BPCC, including the token, is encrypted using TLS 1.2, which is the latest protocol at the time of development. Future enhancements to TLS will be implemented when available.
Password Reset Module Connecting to an External Validation Service
The PRM can be configured to run a script prior to generating a new password for the user for additional security. The PRM will pass the data sent by BPCC to the external validation service, which is designed by the client, and only request a new password if the tool responds with the specified success string. This step is available for clients who require the verification process to be certified locally and entirely within their control.
Password Reset Module Connecting to Active Directory — Domain Server
The PRM runs as a service inside the client network, in an account with Microsoft Active Directory domain administrator privileges. A special user with restricted administrative controls can be created specifically for the service to run in. These credentials are never transferred outside of the client environment, and are only used for communication between the PRM and Microsoft Active Directory Domain Services (AD/DS), adhering to the Microsoft model for security for ADSI object access and services. All settings and data for the service are stored in an encrypted BLOB that is only accessible to the user account running the service through an API. This ensures that all information is irretrievable to other users and no exportable files are created.