Security Policy
This section allows you to configure certain security settings for your contact center. This includes setting up rules for user account lockouts after failed login attempts, defining password requirements (complexity, history, and expiration), managing automatic disabling of inactive accounts, and configuring Multifactor Authentication (MFA) to add an extra layer of security to logins.
Note that the settings you configure here may not be weaker than those defined by your service provider. If service provider settings exist, they are displayed alongside the configurable options in this section. Attempting to set a value weaker than the service provider's default will result in an error message and the change will be blocked.
Your system can be configured for automatic lockout of a user account after a specified number of unsuccessful login attempts. Accounts locked out in this manner can be unlocked manually by an administrator or automatically after a configured timeout period.
You can also configure the system to force your users to change their passwords after a specified number of days, prevent them from submitting previously used passwords, and automatically disable inactive accounts.
Note that your service provider may also impose some password complexity rules, such as minimum password length, mandatory use of various character groups, and exclusion of weak passwords (e.g., usernames). If any such rules are imposed, you cannot change them. You should get descriptions of these rules from your service provider and inform your personnel about them.
To configure security policy settings, select the Security Policy option from the Security menu.
Screen Properties
The Security Policy screen properties are described below.
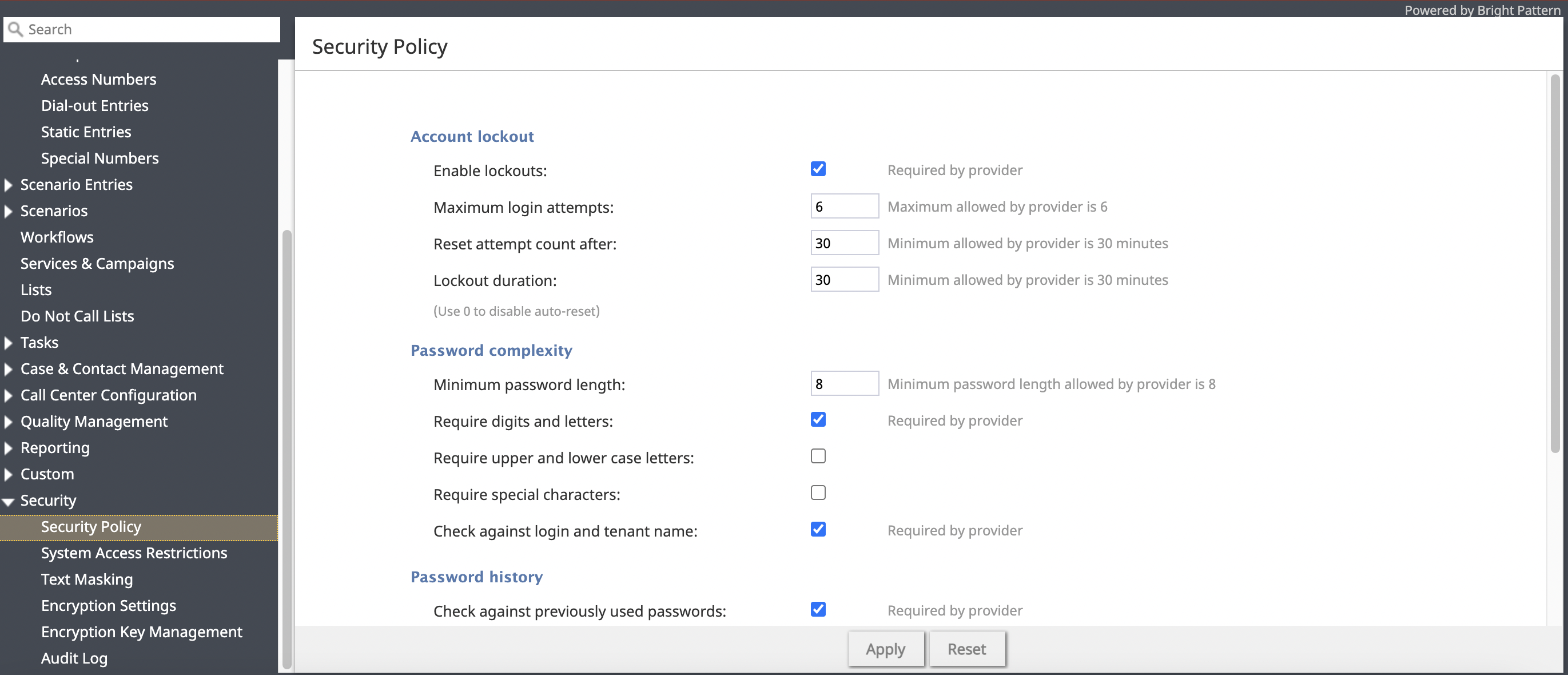
Account lockout
Enable lockouts
Checking this box indicates that the account lockout option is enabled.
To comply with the PCI DSS security standard, this option must be enabled.
Maximum login attempts
This property specifies the number of consecutive unsuccessful login attempts after which the account will be locked out.
To comply with the PCI DSS security standard, set this value to six or greater.
Reset attempt count after
This property specifies the amount of time after which the counter of unsuccessful login attempts will be reset.
Lockout duration
Lockout duration is the amount of time after which a locked-out account will be unlocked automatically. To disable auto-unlocking, set this parameter to “0” (zero), in which case, locked-out accounts can be unlocked manually only.
To comply with the PCI DSS security standard, set this parameter to at least 30 minutes.
Password complexity
This section allows you to define various password complexity requirements; the settings you configure may not be weaker than what is defined by your service provider. Note that passwords can be checked against usernames and your service provider’s list of weak passwords.
Minimum password length
Specify the minimum number of characters required for user passwords.
Require digits and letters
Check this box to enforce that passwords must contain both numeric digits (0-9) and alphabetic letters (a-z, A-Z).
Require upper and lower case letters
Check this box to enforce that passwords must contain both uppercase (A-Z) and lowercase (a-z) letters.
Require special characters
Check this box to enforce that passwords must include at least one special character (e.g., !, @, #, $, %).
Check against login and tenant name
Check this box to prevent users from using their login name or the tenant name as part of their password.
Check against weak password list
Check this box to validate new passwords against the list of commonly used or easily guessable passwords defined by your service provider.
see current list
Click to download the weak passwords list.
Password history
The Password history section allows you to prevent the user from submitting a new password that matches any of the specified number of their previous passwords.
Check against previously used passwords
To comply with the PCI DSS security standard, select the checkbox for Check against previously used passwords.
Number of previously used passwords to keep
To comply with the PCI DSS security standard, set the number to 4 (or greater).
Expiration policy
The Expiration policy section provides control over how often users will be required to change their passwords and after how many days inactive user accounts will be disabled.
Require users to change passwords every
This parameter allows you to specify how often users will be required to change their passwords. To comply with the PCI DSS security standard, set this parameter to no more than 90 days.
Disable inactive accounts after
This parameter allows you to specify after how many days inactive user accounts will be disabled. To comply with the PCI DSS security standard, set this parameter to no more than 90 days.
Exceptions, these user accounts will not be disabled on inactivity
This parameter allows you to define the Contact Center Administrator application users that will be exempt from being disabled on inactivity. Note that API users will no longer be disabled due to inactivity (i.e., API usage now counts as account activity).
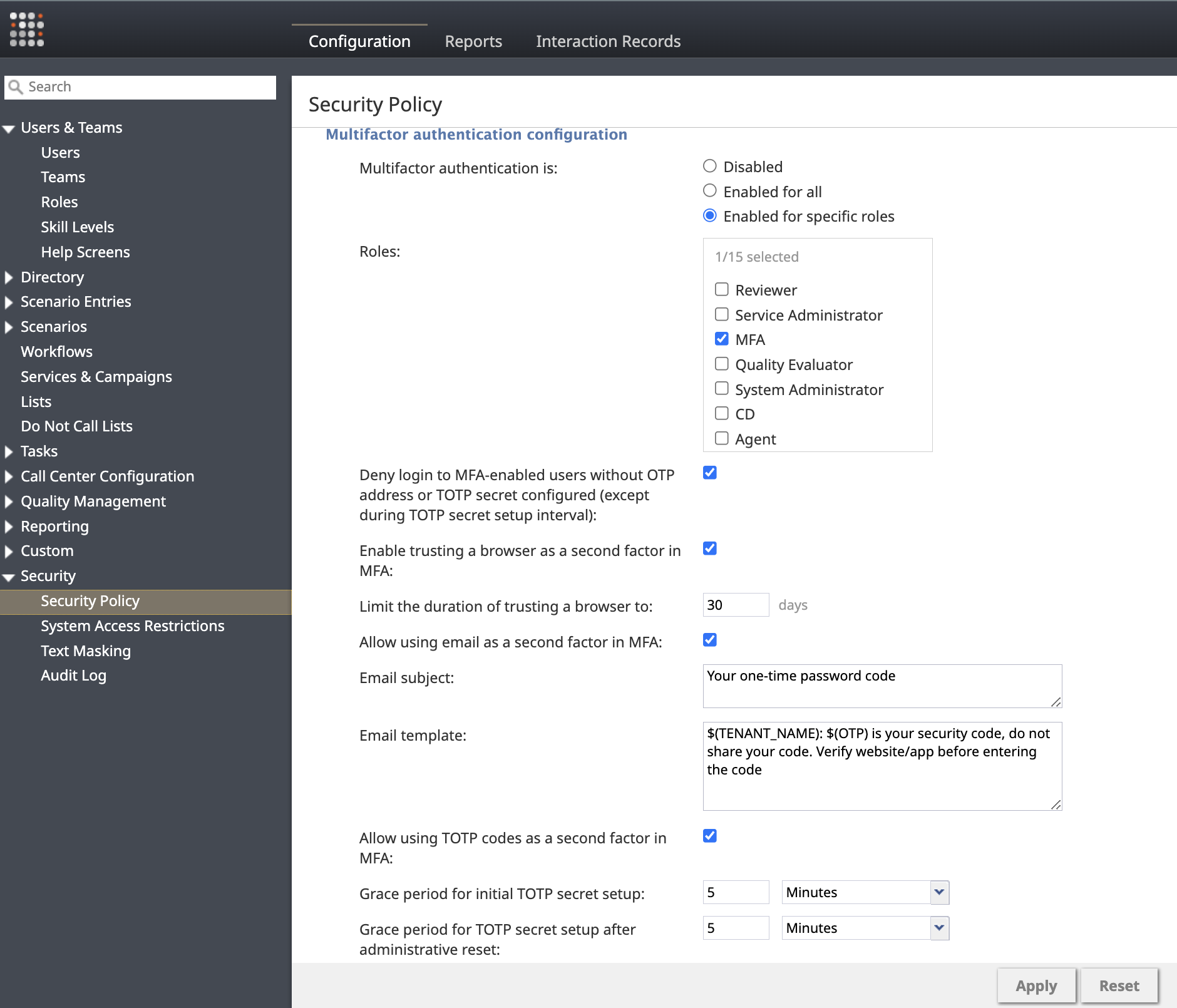
Multifactor authentication configuration
Multifactor authentication (MFA) adds an extra layer of security to user logins by requiring a second form of verification in addition to the password. This section allows you to enable and configure MFA methods for some or all of your contact center users, including options for email-based One-Time Passwords (OTP), Time-based One-Time Passwords (TOTP) from authenticator apps, and the ability to trust specific browsers to reduce MFA prompts.
See How are Multi-Factor Authentication Challenges Issued? for an explanation of when and how users are prompted with MFA challenges.
Multifactor authentication is
Select whether MFA is enabled for all users, or enabled for specific roles.
Roles
Specify the user roles that will be required to use MFA when the Enabled for specific roles option is selected.
Enable trusting a browser as a second factor in MFA
Check this box to allow users the option to "trust" the browser they are using, bypassing MFA prompts on subsequent logins from that same browser for the period defined by Limit the duration of trusting a browser to.
Limit the duration of trusting a browser to
Set the maximum number of days (1-365, default 30) that a browser can remain trusted before the user must provide their second authentication factor.
Allow using email as a second factor in MFA
Check this box to enable the use of One-Time Passwords (OTP) sent via email as an MFA factor. Requires a system email to be configured for your contact center.
Email subject
Specify the subject line for the email containing the OTP code required for MFA.
Email template
Define the body of the email sent with the OTP code to complete an MFA email challenge. You can customize this message using the following variables:
$(TENANT_NAME): The name of the tenant.$(OTP): The one-time password that the user must provide.
For example: $(TENANT_NAME): $(OTP) is your security code, do not share your code. Verify website/app before entering the code.
Allow using TOTP codes as a second factor in MFA
Check this box to allow users to use Time-based One-Time Passwords (TOTP) generated by an RFC 6238-compliant application as their second authentication factor.
Grace period for initial TOTP secret setup
Set the time limit (5 minutes to 7 days, default 24 hours) within which a user must configure their TOTP authenticator app after their account is created or TOTP is first enabled. If they fail to set it up within this period, an administrator must reset their TOTP configuration.
Grace period for TOTP secret setup after administrative reset
Set the time limit (5 minutes to 24 hours, default 24 hours) within which a user must reconfigure their TOTP authenticator app after an administrator has reset their existing TOTP secret. If they fail to set it up within this period, the administrator must reset it again.