| Line 2: | Line 2: | ||
Bright Pattern integrates with Security Assertion Markup Language (SAML) 2.0 identity providers, allowing you to configure single sign-on (SSO) functionality for Agent Desktop (AD) or Contact Center Administrator (Admin). | Bright Pattern integrates with Security Assertion Markup Language (SAML) 2.0 identity providers, allowing you to configure single sign-on (SSO) functionality for Agent Desktop (AD) or Contact Center Administrator (Admin). | ||
| − | + | Note that only one instance can be created per contact center. | |
| − | |||
| − | Note that only one instance can be created per | ||
== Properties == | == Properties == | ||
| Line 14: | Line 12: | ||
=== Name === | === Name === | ||
| − | + | The name of the integration account (any name). | |
=== Enable Single Sign-On === | === Enable Single Sign-On === | ||
| Line 20: | Line 18: | ||
=== Identity Provider Single Sign-On URL === | === Identity Provider Single Sign-On URL === | ||
| − | + | The login URL of your identity provider. | |
=== Identity Provider Issuer === | === Identity Provider Issuer === | ||
| − | + | The unique identifier of your identity provider. | |
=== Identity Provider Certificate === | === Identity Provider Certificate === | ||
| − | + | The contents of the SAML certificate that the identity provider uses to sign the SAML tokens that it sends to the application. | |
=== Enable Just-in-time user provisioning === | === Enable Just-in-time user provisioning === | ||
Select this checkbox to enable Just-in-time user provisioning (JIT). JIT user provisioning automatically creates call center users on the first SSO login attempt authorized by the identity provider. | Select this checkbox to enable Just-in-time user provisioning (JIT). JIT user provisioning automatically creates call center users on the first SSO login attempt authorized by the identity provider. | ||
| + | |||
| + | Note that JIT is disabled if SSO is not enabled. | ||
| + | |||
| + | You should enable JIT user provisioning if: | ||
| + | * JIT user provisioning is enabled for the application | ||
| + | * The tenant URL is known (extracted from the domain name, tenantUrl parameter, or SAML additional parameter) | ||
| + | * The user with login Id does not exist in that tenant | ||
| + | * SAML assertion is signed and valid | ||
| + | |||
| + | When creating a new user using JIT user provisioning: | ||
| + | * The newly created user should copy assignments (e.g., roles, teams, skills, etc.) from the selected user template | ||
| + | * User contact information should be copied from SAML assertion. As a minimum, this contact information should include first name, last name, login ID, and email address (others are optional) | ||
| + | * Once the user is created, that user should be logged in immediately | ||
=== Use Template === | === Use Template === | ||
| − | SSO templates are disabled. | + | Select this checkbox to copy assignments (e.g., roles, teams, skills, etc.) from a specific user, and apply them to new call center users created by JIT user provisioning. |
| + | |||
| + | Note that SSO templates are required if JIT user provisioning enabled. SSO templates are disabled if JIT user provisioning is disabled. | ||
| + | |||
| + | |||
| + | |||
| + | |||
| + | |||
</translate> | </translate> | ||
Revision as of 23:05, 1 May 2019
<translate>= Single Sign-On Integration = Bright Pattern integrates with Security Assertion Markup Language (SAML) 2.0 identity providers, allowing you to configure single sign-on (SSO) functionality for Agent Desktop (AD) or Contact Center Administrator (Admin).
Note that only one instance can be created per contact center.
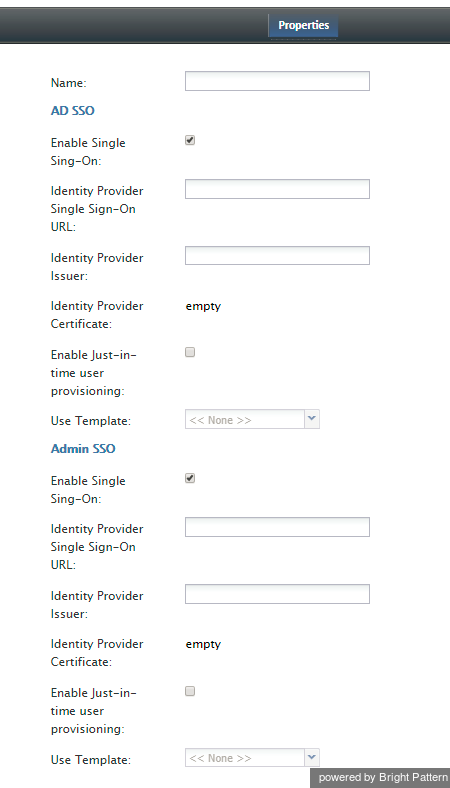
Properties
The properties of Single Sign-On integration accounts are described as follows. The properties are the same for both AD SSO and Admin SSO.
Name
The name of the integration account (any name).
Enable Single Sign-On
Select the checkbox to enable single sign-on functionality.
Identity Provider Single Sign-On URL
The login URL of your identity provider.
Identity Provider Issuer
The unique identifier of your identity provider.
Identity Provider Certificate
The contents of the SAML certificate that the identity provider uses to sign the SAML tokens that it sends to the application.
Enable Just-in-time user provisioning
Select this checkbox to enable Just-in-time user provisioning (JIT). JIT user provisioning automatically creates call center users on the first SSO login attempt authorized by the identity provider.
Note that JIT is disabled if SSO is not enabled.
You should enable JIT user provisioning if:
- JIT user provisioning is enabled for the application
- The tenant URL is known (extracted from the domain name, tenantUrl parameter, or SAML additional parameter)
- The user with login Id does not exist in that tenant
- SAML assertion is signed and valid
When creating a new user using JIT user provisioning:
- The newly created user should copy assignments (e.g., roles, teams, skills, etc.) from the selected user template
- User contact information should be copied from SAML assertion. As a minimum, this contact information should include first name, last name, login ID, and email address (others are optional)
- Once the user is created, that user should be logged in immediately
Use Template
Select this checkbox to copy assignments (e.g., roles, teams, skills, etc.) from a specific user, and apply them to new call center users created by JIT user provisioning.
Note that SSO templates are required if JIT user provisioning enabled. SSO templates are disabled if JIT user provisioning is disabled.
</translate>