Multi-Factor Authentication
Multi-Factor Authentication (MFA) adds an extra layer of security to user logins by requiring users to provide two or more verification factors. BPCC natively supports Time-based One-Time Passwords (TOTP) via authenticator apps and/or email verification codes as second factors. See Security Policy > Multi-Factor Authentication Configuration for configuration options.
Please note that if you are using Single Sign-on, MFA, if enabled, would only apply to the users logging in via bypass SSO capability. For SSO users, MFA would have to be set up in the corresponding SSO identity provider.
How do I set up Multi-Factor Authentication
- Contact your service provider to enable the Multi-Factor Authentication feature for your contact center.
- Navigate to the Multi-Factor Authentication Configuration section of your contact center's Security Settings. Choose whether to enforce MFA for All Users or only for users assigned to specific Roles.
- Select Methods: Within the MFA configuration, enable your preferred second authentication factors: TOTP (Authenticator App), Email, or both.
- If TOTP is enabled, users will be prompted to configure TOTP on their next login within the setup grace period.
- The below section How are Multi-Factor Authentication Challenges Issued? explains what will happen when users attempt to log in once MFA is enabled.
How do I Reset the TOTP Grace Period for a User?
If a user missed the initial TOTP setup grace period, or needs to reconfigure their TOTP secret (e.g. lost/replaced device), follow these steps:
- Navigate to Users & Teams page and select the user requiring the reset.
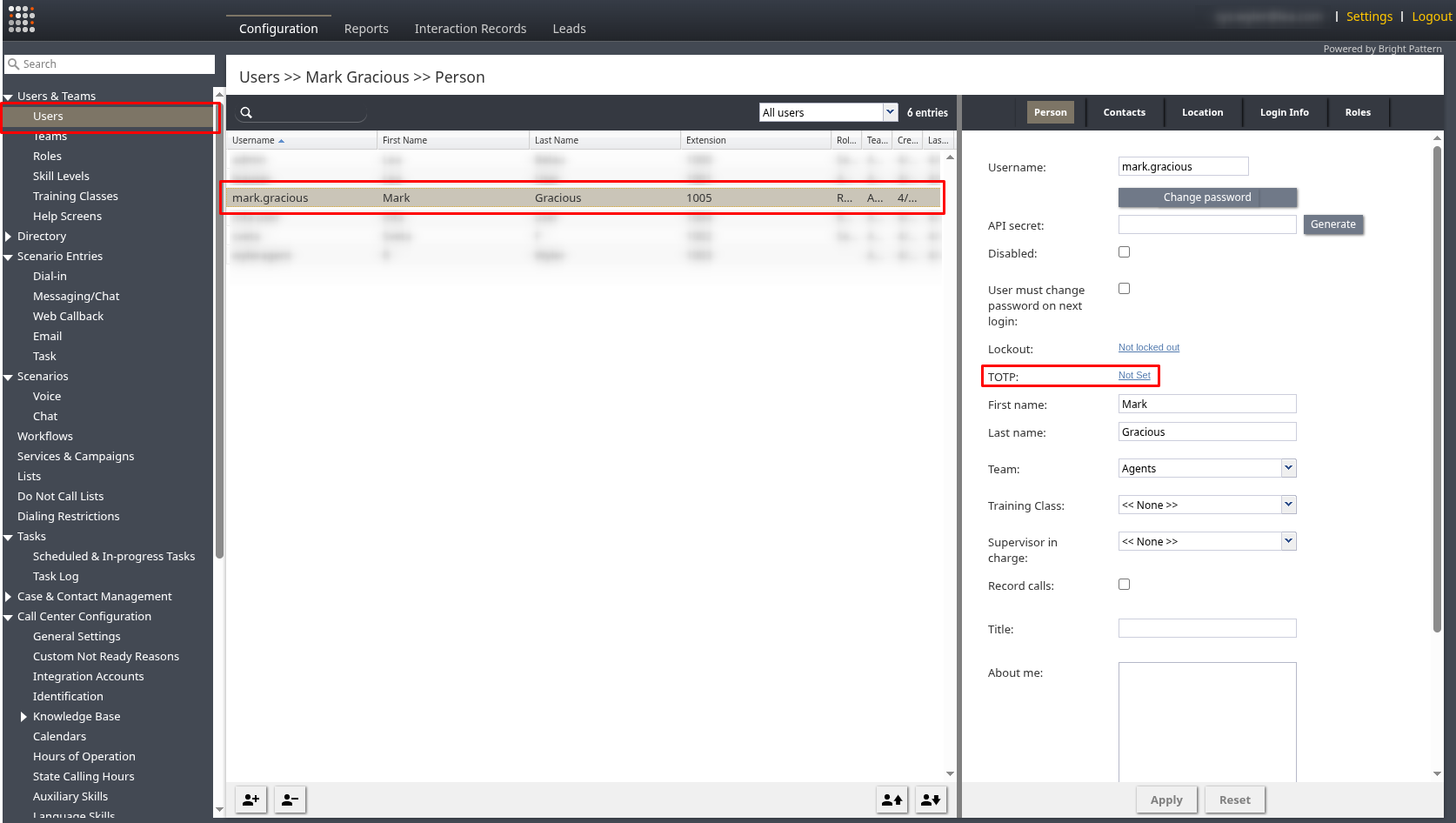
Select the user and open the Person tab - On their user Person tab, find the TOTP status setting. Click the link next to it (it will show as "Set" if previously configured, or "Not Set" if not).

Click the link next to the TOTP setting - Click Reset to reset the user's TOTP configuration grace period. They will be prompted to set up a new TOTP secret on their next login attempt that occurs within the administrative reset grace period.
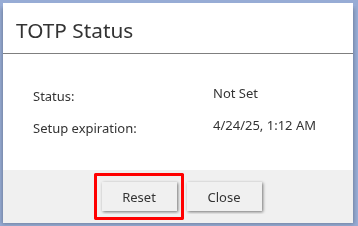
Click "Reset" to reset the TOTP configuration grace period
How are Multi-Factor Authentication Challenges Issued?
After a user successfully provides their correct username and password, the system determines whether and how to issue an MFA challenge according to the following logic:
Check if MFA is Required for the User
- If NO: The user is allowed to log in without an MFA challenge.
- If YES: The user is issued an MFA challenge based on whether TOTP, Email, or both are enabled as second authentication factors.
Both TOTP and Email Challenges Enabled
If both TOTP and email are enabled, users will be challenged according to the following scenarios:
User with a configured TOTP secret
- Challenge: Prompt user to provide the TOTP code from their authenticator application.
- Result: User is granted access if the provided code is correct; otherwise, access is denied.
User with an email address but without a TOTP secret
- Challenge: Send an OTP to the user's email address.
- Result:
- If user provides the correct OTP, prompt them to set up TOTP (even if the TOTP grace period has expired) and grant access after successful TOTP setup and confirmation.
- Access is denied if the user cannot provide the correct OTP.
User has neither a TOTP secret nor an email address configured
- If they are within the TOTP setup grace period:
- Prompt the user to set up TOTP and grant access after successful TOTP setup and confirmation.
- Access is denied if the user is not within the TOTP setup grace period.
Only TOTP Enabled
If only TOTP is enabled as an MFA challenge, users will be challenged as follows:
User with a configured TOTP secret
- Challenge: Prompt user to provide the TOTP code from their authenticator application.
- Result: User is granted access if the provided code is correct; otherwise, access is denied.
User without a TOTP secret
- If they are within the TOTP setup grace period:
- Prompt the user to set up TOTP. Grant access after successful TOTP setup and confirmation.
- Access is denied if the user is not within the TOTP setup grace period.
Only Email Enabled
If only Email is enabled as an MFA challenge, but TOTP is disabled, the user will be challenged as follows:
User has an email address configured
- Challenge: Send an OTP to the user's email address.
- Result: User is granted access if they can provide the correct OTP; otherwise, access is denied.
User does not have an email address configured
- Challenge: None possible (Email OTP cannot be sent).
- Result: Access is denied.
< Previous | Next >